Data Loss Prevention
Data Loss Prevention
Avoid data leaks on remote endpoints or remote desktop connections. Support a wide range of remote access solutions.
Secures all potential data leakage points, such as email, cloud services, messaging apps, external devices, and network transfers. Prevent unauthorized sharing through web applications, social media, printing, or removable media.
Provides real-time reporting of unauthorized data access and attempted data leaks from all outpoints. React fast thanks to real-time detection of suspicious activities and immediate email alerts.
Enables classified access control based on file type, user roles, and time-specific permissions. Classify sensitive files and emails with powerful content inspection with predefined templates or custom rules and dictionaries.
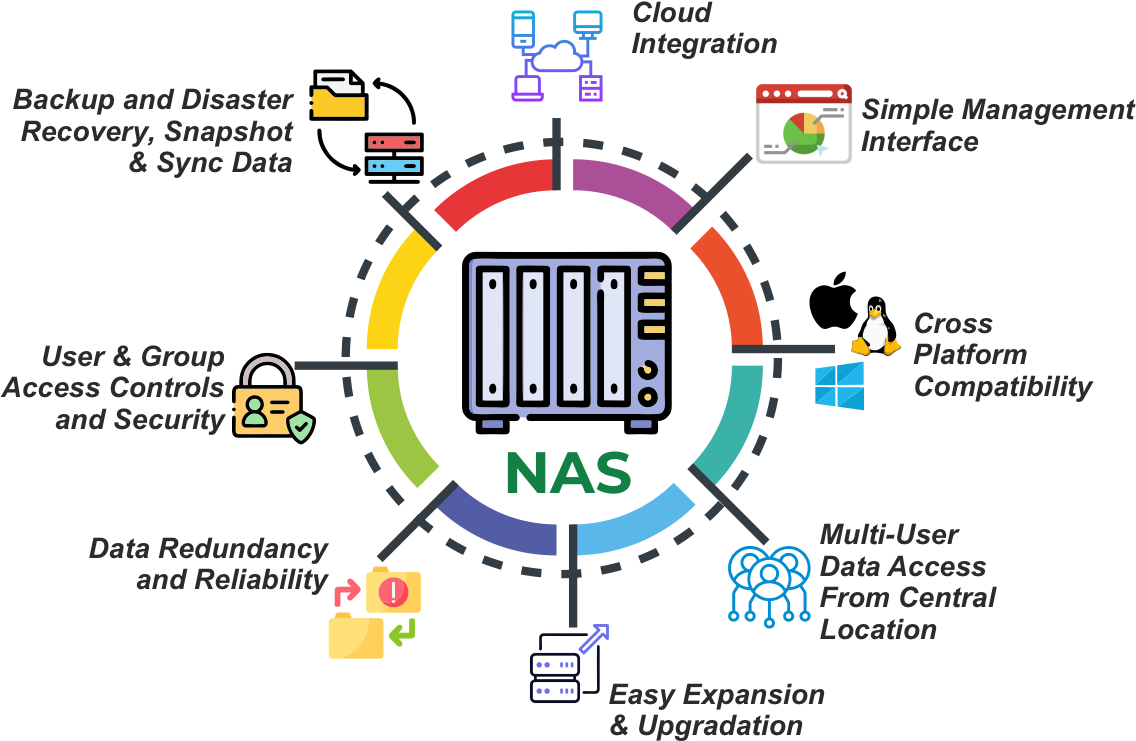
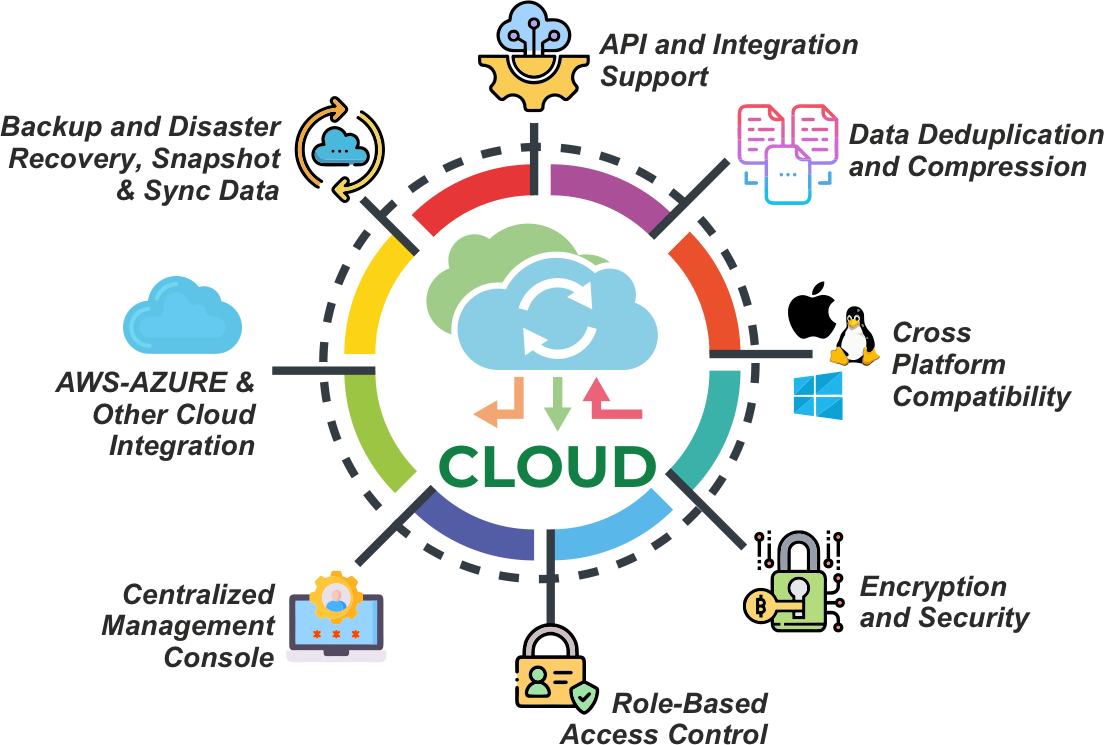
 Data Storage & Management
Data Storage & Management